Network Layer [1]
- Provides the upper layers with independence from data transmission and physical networking technologies
- Responsible for sending data from source to destination (this includes the nodes in between and is therefore not end-to-end)
- Responsible for requesting network facilities such as priority, bit-rate, etc…
- Responsible for routing
Routing [1]
- Autonomous System (AS) – set of networks and routers operated by a single organization
- Interior Router Protocol (IRP) – passing routing information within an autonomous system
- Exterior Router Protocol (ERP) – passing routing information between different autonomous systems
Routing Approaches [1]
- Distance Vector Routing – each node exchanges information with its neighboring nodes (ex: Routing Information Protocol, RIP)
- Link-state Routing – sends link costs of each of its network interfaces to all routers (not just neighboring). Typically used with a Dijkstra-based algorithm (ex: Open Shortest Path First, OSPF)
- Path-vector Routing – router provides information about which networks can be reached by a given router and the autonomous systems that must be crossed (ex: Border Gateway Protocol, BGP)
 [1]
[1]
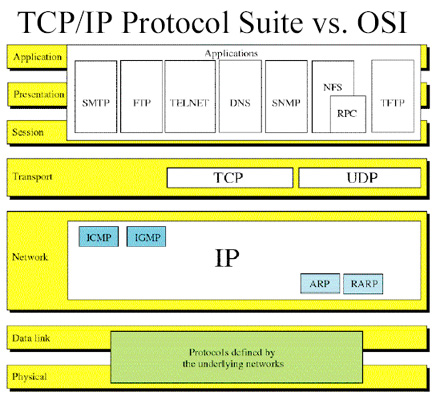
Internet Architecture
In a TCP/IP internet, IP Routers provide interconnection among physical networks.[1]
Internet Protocol (IP)
- The most-widely used internetworking protocol
Internetworking Requirements [1] – accommodate the differences among the networks which form the intenetwork.
- different addressing schemes
- different maximum packet size
- different network access mechanism
- different timeouts
- different transmission modes (connection oriented, connectionless)
- error control
- flow control
 [1]
[1]
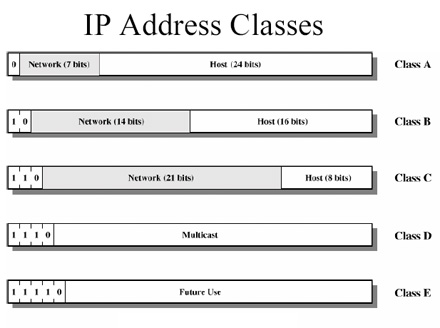
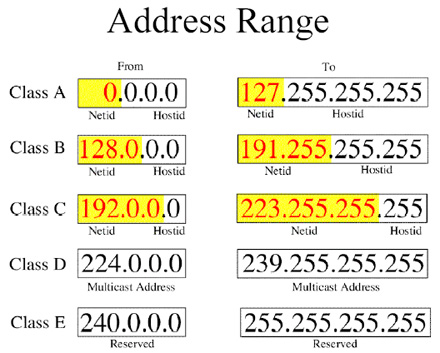
1. Different Addressing Scheme [1]
- Introduce IP Address as a global address
- All hosts on the internet must have a unique IP address
- NOTE: Techniques such as IP-forwarding allow private IP addresses that might be duplicated somewhere else.
 [1]
[1]
 [1]
[1]
Subnet and Subnet Masks [1]
- Allow arbitrary complexity of internetworked LANs within an organization
- Insulate overall internet from growth of network numbers and routing complexity
- To rest of internet, site looks like single network
- Each LAN is assigned a subnet number
- Host portion of address is partitioned further into subnet number and host number
- Local routers route within subnetted network
- Subnet mask indicates which bits are subnet number and which are host number by doing a bitwise AND
2. Different Maximum Size [1]
Different networks have different Maximum Transmission Unit (MTU) sizes. What if a packet reaches a network and it exceeds the networks MTU? This can be solved with the following solution:
- Use fragmentation to split large packets into smaller ones
- Use reassembly at the destination only to put the fragments together and build the original packet
Fragmentation and Reassembly [1]
When to re-assemble
- At destination – results in packets getting smaller as data traverses internet
- Intermediate re-assembly
- Need large buffers at routers
- Buffers may fill with fragments
- All fragments must go through same router
- Inhibits dynamic routing
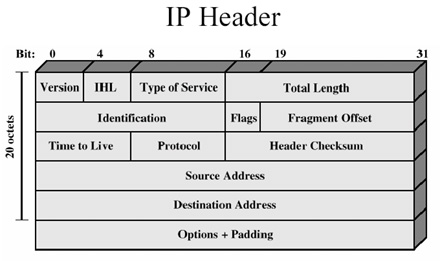
IP Fragmentation [1]
- IP re-assembles at destination only
- Uses fields in header
- Data Unit Identifier (ID)
- Identifies end system originated diagram
- Source and destination address
- Protocol layer generating data (ex: TCP)
- Identification supplied by that layer
- Identifies end system originated diagram
- Data Length
- Length of user data in octets
- Offset
- Position of fragment of user data in original datagram
- In multiples of 64 bits (8 octets)
- More flag
- Indicates that this is not the last fragment
- Data Unit Identifier (ID)
Dealing with Failure [1]
- Re-assembly may fail if some fragments get lost
- Re-assembly time out
- Assigned to first fragment to arrive
- If timeout expires before all fragments arrive, discard partial data
3. Different Network Access [1]
- Solved by abstracting networking functions in the networking layer, and relying on Data Link Layer for networking access
- Routers handle the difference in network access mechanism.
Address Mapping [1]
- Sometimes, in order to reach a destination, there is no need to go through an IP router.
- In such a case, the physical address can be used directly
ARP – Address Resolution Protocol
Reverse ARP
4. Different Timeout [1]
- Problem: different networks use different timeout mechanisms.
- Solution: Introduce the concept of Datagram Lifetime.
- Datagrams could loop indefinitely
- Consumes resources
- Transport protocol may need upper bound on datagram life
- Datagram marked with lifetime
- Time to Live (TTL) field in IP
- Once lifetime expires, datagram discarded (not forwarded)
- Hop count
- Decrement time to live on passing through each router
5. Different Transmission Modes [1]
- Use a connectionless architecture
- Advantage:
- Flexibility
- Robust
- No unnecessary overhead
- Disadvantages
- Not guaranteed delivery
- Not guaranteed order of delivery
- Reliability is responsibility of upper layers (ex: TCP)
6. Error Control [1]
- Minimal error control, done only for the header
- Router should attempt to inform source if packet discarded (using ICMP)
- Not guaranteed delivery
- May inform higher layer protocol
7. Flow Control [1]
- Â Allows routers and/or stations to limit rate of incoming data
- Limited in connectionless systems
- Send flow control packets
- Requesting reduced flow
- ex: ICMP
—[1] Prof. Shervin Shirmohammadi, University of Ottawa CEG4183 Course Notes, Lecture 2